Table of Links
V. Analysis of EZchain's Performance, Security and Decentralization
VI. Simulation Experiments of EZchain
VII. Conclusions, Acknowledgements, and References
II. RELATED WORKS
Among works closely related to EZchain, the Vapor blockchain, introduced by Ren et al. [2], [3], stands out. Vapor pioneered the “values”-like concept, termed “adaptive sharding”. Despite its claimed scale-out performance, our approach diverges in key aspects. Firstly, Vapor’s block size varies and escalates with node count expansion, as detailed in its block data structure design [3]. Secondly, lacking targeted algorithmic refinement for value transfer, Vapor does not match EZchain’s performance levels. More importantly, as the system operates, the communication and storage complexity of Vapor will tend towards O(n), whereas EZchain will approach a constant independent of n.
In blockchain scalability research, initial efforts concentrated on expanding block size, enhancing block generation rates, and expediting transaction confirmations in layer-1 [4]– [9]. These endeavors primarily optimized Bitcoin’s Nakamoto consensus [10]. Strategies included decoupling leader election from block consensus [4] and integrating BFT-like algorithms to reformulate consensus mechanisms [5], [6], [8]. Experimental findings indicate these methods not only achieved breakthroughs in consensus efficiency but also reached transaction processing speeds rivaling centralized systems like PayPal [5].
Further advancements in blockchain performance have led to diverse solutions, including sharding, DAG-based blockchains, off-chain mechanisms, cross-chain interoperability, and Zero-Knowledge Proofs technology [11]–[29]. Each aims to surmount the inherent bottlenecks in transmission, storage, and verification processes.

DAG-based blockchains, diverging from conventional chain structures, utilize a directed acyclic graph (DAG) for block storage [17], [18], [32], [33]. This architecture allows nodes to add blocks efficiently and concurrently, significantly enhancing block generation efficiency and, in theory, approaching the network’s transmission capacity. However, two critical challenges persist: 1) Optimizing bandwidth utilization in DAGbased systems demands a delicate balance among consensus efficiency, verification speed, and transmission capability; 2) There is yet to be a universally accepted solution for transaction ordering in DAG-based blockchains.
Off-chain technologies alleviate the main chain’s workload, thereby enhancing scalability, efficiency, and privacy within the blockchain system [19]–[21], [34]. Prominent off-chain solutions encompass sidechains, state channels, and lightning networks. Their point-to-point transmission and verification, unencumbered by consensus protocols, present an efficient strategy to overcome various system bottlenecks. Nonetheless, off-chain methods grapple with challenges such as security and trust in environments independent of the main chain’s security guarantees, and the reconciliation of off-chain and on-chain data consistency.
Cross-chain technology facilitates interoperability between distinct blockchain networks through intermediate layers or protocols [22]–[25], [35]–[37]. This technology enables blockchains to share transactions and states. Nevertheless, prevalent cross-chain solutions often depend on centralized validators, a deviation from the decentralization ethos and a compromise on blockchain’s inherent security. Furthermore, trustless cross-chain models are associated with elevated costs.
Zero-Knowledge Proofs (ZKPs) are heralded as potential universal solutions for enhancing blockchain scalability and facilitating cross-chain interoperability [25]–[29], [38]–[41]. They offer the dual benefits of safeguarding user privacy and reducing verification and storage demands. However, the generation and validation of ZKPs, particularly complex ones, can be computationally intensive and time-consuming, posing potential performance bottlenecks for the system.
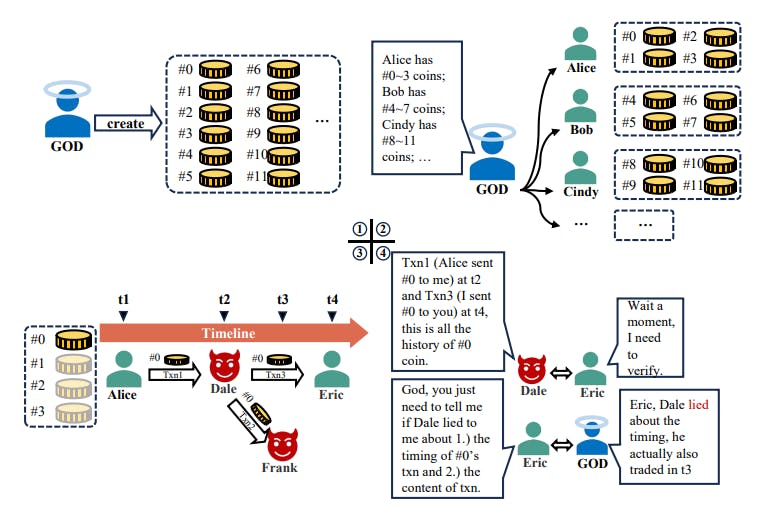
III. SYSTEM MODELS
Following the convention, it is necessary to standardize and define the models of network and threats that the EZchain system is confronted with.
A. Network Model
The communication network of EZchain is composed of several consensus nodes and account nodes. All nodes can use broadcasting (e.g., gossip protocol) or peer-to-peer (P2P) mode for message transmission. We assume that this network is weakly synchronous, and communication between nonbyzantine fault nodes (i.e., honest nodes) is synchronous. Each honest node has a certain number of honest neighboring nodes, and the network connections between them are robust and unimpeded.
B. Threat Model
EZchain tolerates up to f = λn byzantine nodes, where λ = 1/3 (for BFT-like backbone consensus algorithm) or λ = 1/2 (for PoW-like backbone consensus algorithm). The byzantine node can make any deviation from the protocol. In addition, the adversary cannot break our cryptographic assumptions in polynomial-time.
Authors:
(1) Lide Xue, University of Science and Technology of China, Hefei, China ([email protected]);
(2) Wei Yang, University of Science and Technology of China, Hefei, China ([email protected]);
(3) Wei Li, University of Science and Technology of China, Hefei, China ([email protected]).
This paper is