Authors:
(1) Zhongtang Luo, Purdue University ([email protected]);
(2) Rohan Murukutla, Supra ([email protected]);
(3) Aniket Kate, Purdue University / Supra ([email protected]).
Table of Links
II. Expectations of Blockchain Accessibility
III. Approach I: Maintain a Ledger Locally - Run a Full Node
IV. Approach II: Query a Third-Party Ledger-Node-As-A-Service (NAAS)
V. Approach III: Light Node - External Query & Local Verification
VI. Concluding Remark and References
Abstract—While much research focuses on different methods to secure blockchain, information on the chain needs to be accessed by end-users to be useful. This position paper surveys different ways that end-users may access blockchains. We observe that between the two extremes of running a full node and fully utilizing a trusted third-party service, many solutions regarding light nodes are emerging. We analyze these solutions based on three basic properties of web communication: integrity, availability and privacy. We conclude that currently, the best way to access a blockchain while maintaining these three properties is still to run a full node. We consider it essential that future blockchain accessibility services should be built while considering these three expectations.
I. INTRODUCTION
A blockchain is a group of nodes trying to maintain a publicly verifiable ledger of transactions protected from tampering. After its first proposal as Bitcoin [41] in 2009, blockchains have gained much popularity as financial instruments. The success of most well-known blockchains, such as Bitcoin and Ethereum [20] can largely be attributed to their decentralized nature and their capabilities to handle complex transactions with advanced cryptographic primitives. With currently a large market, blockchains have the potential to become a leading innovation in the finance and e-commerce sectors in the 21st century.
Much existing blockchain infrastructure research and innovation focus on secure and efficient ways for participating nodes to maintain the public ledger (known as a layer-1 protocol). However, we note that fetching information from a well-maintained ledger is also a non-trivial issue. Ensuring that blockchains stay accessible to every user is essential if blockchains are to play a bigger role in everyday life—a public ledger is, by definition, only useful as long as people can interact with it.
Given the recent growing public interest in blockchains, more users are interacting with blockchains every month, with as many as 875,000 transactions a day for popular blockchains such as Ethereum [20]. Trying to extract useful information from a flood of transactions requires powerful hardware for even a standard blockchain user who does not engage in profit-generating behavior (like mining), and it appears that the incentive mechanism in most blockchains is not equipped to deal with the issue.
In most blockchain protocols, such as Bitcoin and Ethereum, participating nodes (miners in proof-of-work systems and validators in proof-of-stake systems) are incentivized to maintain the ledger by earning a small fee when proposing a new block to the ledger. While participating nodes in these blockchain protocols are incentivized to collect transactions and broadcast raw blocks to ensure their profit, they are not incentivized to publish refined information about the ledger they maintain. Consider these two examples: (1) A user wants to know how many coins there are in their Bitcoin wallet. (2) A user wants to know the current status of a smart contract they want to execute.
Similar to these examples, most information users want to know is not directly related to the raw blocks that miners and validators publish. The users may entrust their assets fully to a third-party exchange and obtain information from the exchange, but the approach is significantly risky as evidenced by the recent FTX collpase [31]. Therefore, blockchain users need to devise a method to extract such information from blocks, either through some computation power that they own or by relying on a third-party service provider.
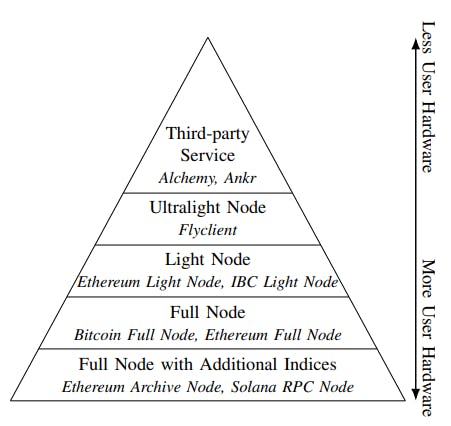
In this paper, we compare the two current methods in practice that users adopt to obtain refined information from blockchains. One method involves running a full node locally. This method is usually capable of extracting much information from the blockchain without external reliance. In some cases though, additional indices are kept to ensure a faster query, such as Ethereum archive nodes and Solana RPC nodes. The other method is to rely on a third-service provider. We notice the trend that as the cost of running a full node grows, especially in Ethereum, many users are turning to third-party services, which carry their own security risks. We observe that running a full node and fully utilizing a trusted third-party service represent two extremes regarding blockchain accessibility: one with minimal reliance and maximal hardware requirement and one with maximal reliance and minimal hardware requirement.
We also notice that when the required data on the blockchain is specific and limited, like when the users only care about one address that they own, specific wallet software is available to the users. While some of the wallet software queries an external node directly for data, others may download a portion of the blockchains and directly analyze it for the information the users care about. We categorize the software as specific light nodes. Meanwhile, we outline a recent trend in realizing a universal light node that can provide any information to
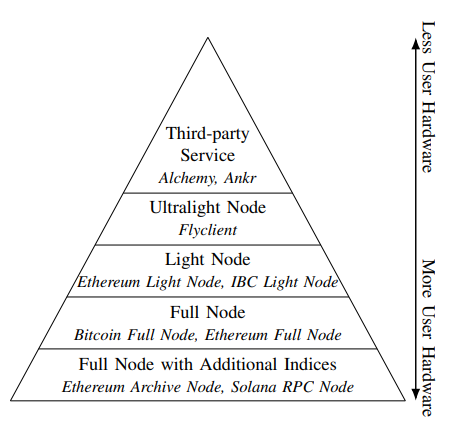
users, not just one address [12], such as the one proposed by Ethereum [24]. Current research also includes so-called ultralight nodes, such as Flyclient [10], that step closer to relying on a third-party service that provides additional context for verification (also known as a prover in this context) than traditional light nodes that rely only on full nodes. Figure 1 shows a list of different methods to access blockchains.
We think that amid many ways to access blockchains, it is still important to examine the basics of any web service: integrity, availability, and privacy. The blockchain itself is a technology of decentralization, yet too much reliance on a small number of third parties goes against this premise. Without a method to verify the correctness of data, integrity may be compromised if the said third parties provide incorrect data. With too much dependence on selected third parties to provide accessibility, availability may be impacted if they are unable or unwilling to provide service. Privacy is also a concern that needs addressing when querying any third party.
We examine existing protocols in the market and find that many of them may be flawed in at least one of these aspects. Currently, the best way to access a blockchain while maintaining integrity, availability and privacy is still to run a full node locally. We consider it important to pay attention to these three aspects when designing any protocol to interact with blockchains to ensure functionality.
This paper is available on arxiv under CC BY-NC-ND 4.0 DEED license.